Introducing Fuzzstorm: The Ultimate Fuzzing Tool with Soft 404 Detection and Stunning HTML Reports
Discover Fuzzstorm, a new fuzzing tool designed to simplify web application testing with comprehensive scans, unique soft 404 detection, and beautiful HTML reports for easy result interpretation.
Introducing Fuzzstorm: Revolutionizing Fuzzing with Simplicity, Precision, and Beautiful Reports 🌩️
In the fast-paced world of cybersecurity, fuzzing is a critical technique for uncovering hidden vulnerabilities in web applications. Yet, many fuzzing tools are complex, prone to false positives, or require endless configuration tweaks. Enter Fuzzstorm, a game-changing fuzzing tool designed to simplify the process, deliver accurate results, and present findings in a visually stunning way. Whether you’re a pentester, bug bounty hunter, or developer, Fuzzstorm is here to make your life easier.
Why Fuzzstorm? 🚀
Tools like Wfuzz and FFUF are powerful, but their complexity can lead to missed endpoints or results cluttered with false positives if parameters aren’t perfectly tuned. I built Fuzzstorm to address these challenges, focusing on simplicity, accuracy, and user-friendly output. Here’s what sets Fuzzstorm apart:
1. Comprehensive Scans by Default ⚙️
Forget the frustration of missing a critical parameter and ending up with incomplete scans. Fuzzstorm runs all possible scans by default, ensuring you uncover every directory, file, or API endpoint without needing to juggle countless flags. From beginners to seasoned pros, Fuzzstorm delivers thorough results effortlessly.
2. Soft 404 Detection: Eliminate False Positives 🚫
Soft 404s—pages that return a 200 OK status but act like 404 errors—are the bane of fuzzing. They flood your results with noise, wasting time and obscuring real findings. Fuzzstorm’s innovative soft 404 detection filters out these deceptive responses, giving you clean, actionable results. This feature alone makes Fuzzstorm a standout in the fuzzing world.
3. Stunning HTML Reports for Easy Analysis 📊
Fuzzstorm doesn’t just find vulnerabilities—it presents them beautifully. At the end of each scan, Fuzzstorm generates a gorgeous HTML report that organizes results in a clear, visually appealing format. These reports make it easy to interpret complex data, share findings with teams, or present results to clients. No more sifting through raw logs—Fuzzstorm’s reports are designed for clarity and impact.
4. Built for Ease and Efficiency ⚡
Fuzzstorm is crafted for usability, with an intuitive interface and a streamlined workflow. Whether you’re fuzzing directories, subdomains, or parameters, Fuzzstorm balances ease of use with high performance. Written in Python, it handles large wordlists with speed and reliability.
Why Soft 404 Detection Matters
Soft 404s are a major hurdle in fuzzing. Many servers return 200 status codes for non-existent pages, tricking tools into logging them as valid. This creates a flood of false positives, making it harder to spot real vulnerabilities. Fuzzstorm’s soft 404 detection eliminates these distractions, ensuring your results are accurate and trustworthy.
Why HTML Reports Are a Game-Changer
Fuzzing often produces overwhelming amounts of data, especially when scanning large applications. Fuzzstorm’s HTML reports transform this data into a visually intuitive format, with tables, charts, and clear categorizations of findings. Whether you’re presenting to a client, collaborating with a team, or documenting for a bug bounty submission, these reports save time and elevate your work’s professionalism. Plus, they’re easy to share and view on any device, making Fuzzstorm a must-have for modern security workflows.
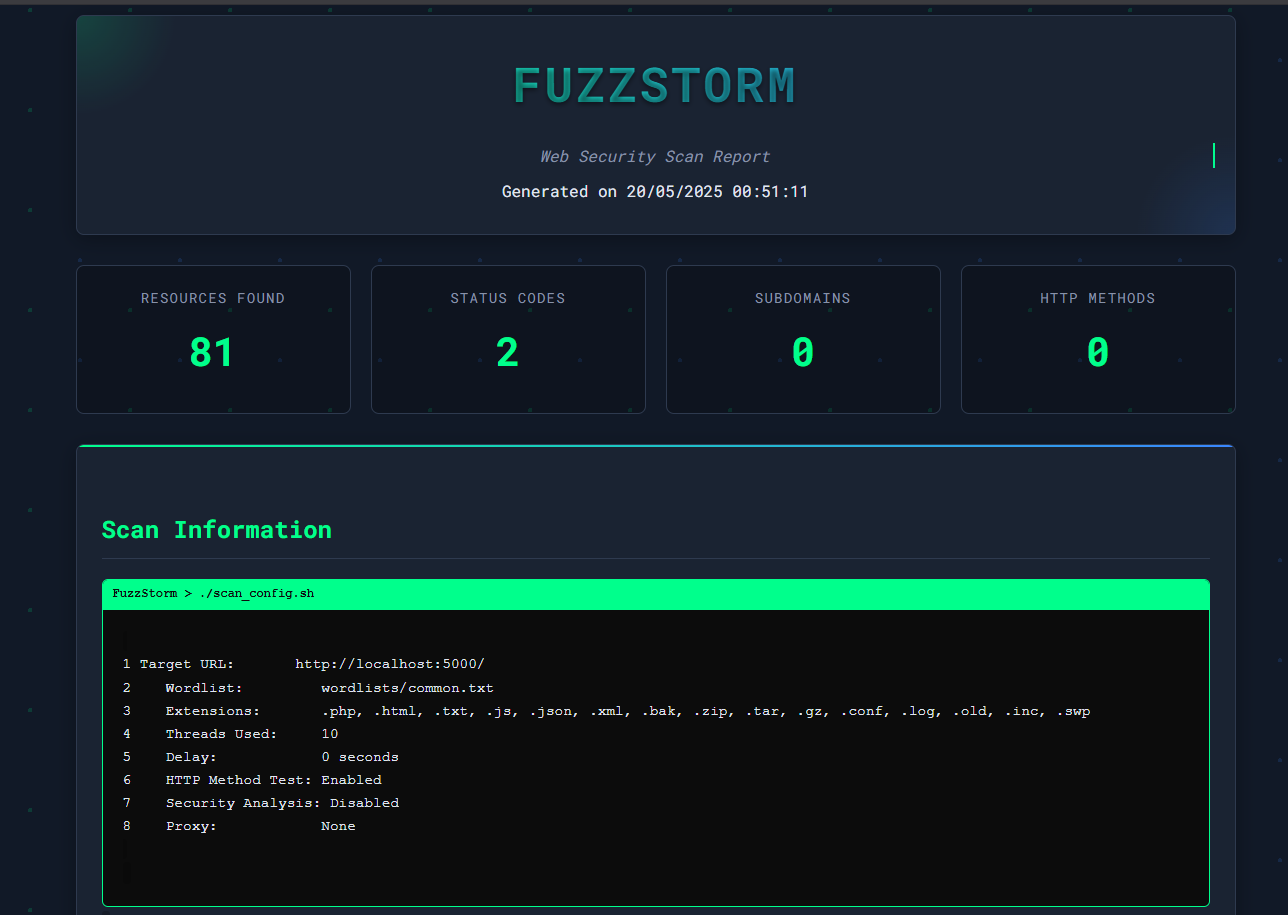
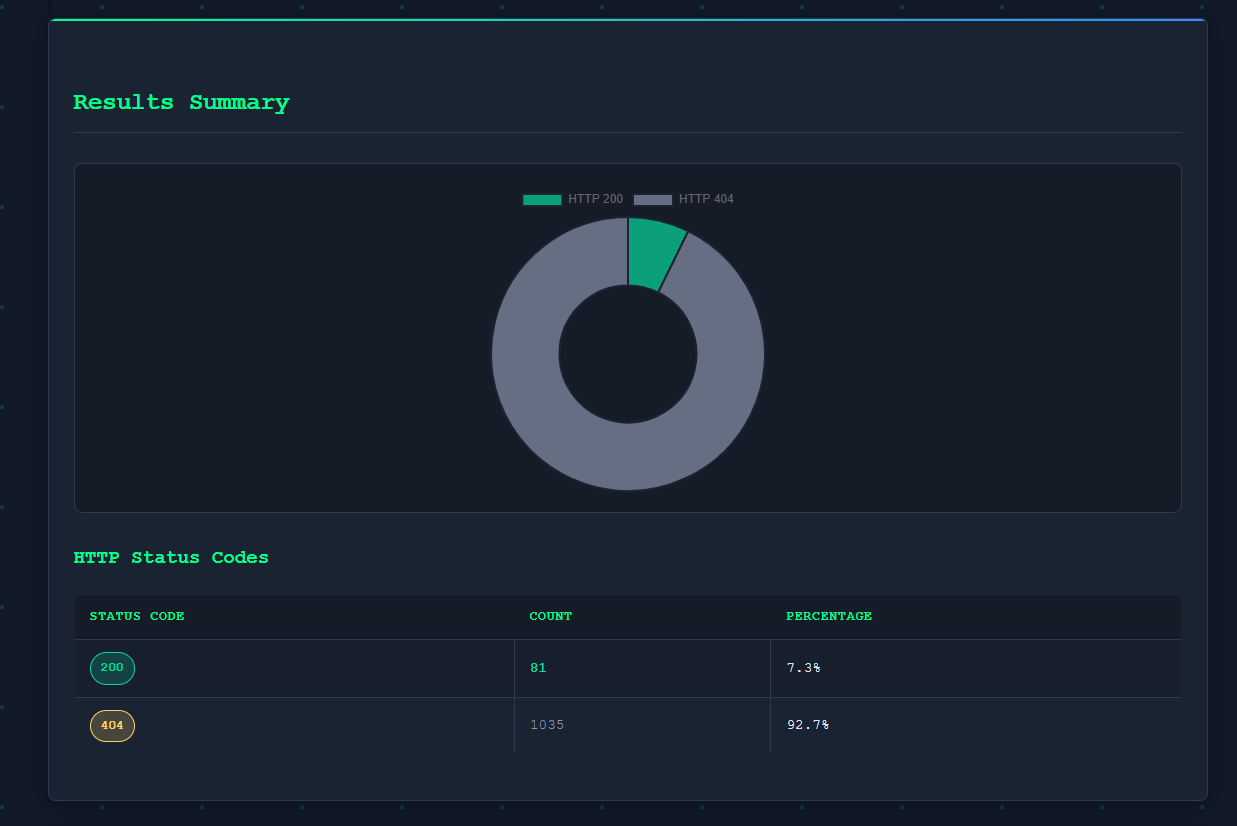
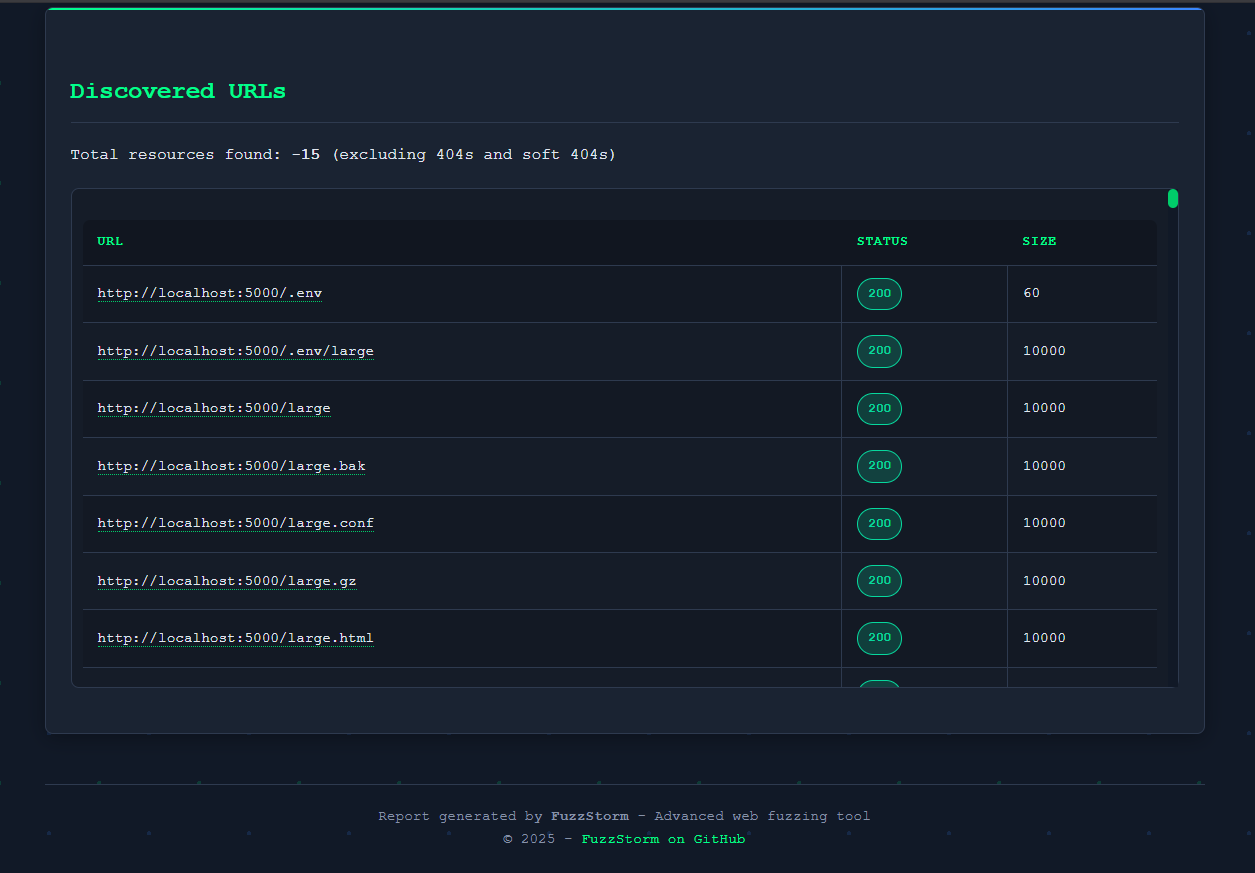 Sample HTML report generated by Fuzzstorm, showcasing organized and visually appealing results with status codes and resource summaries.
Sample HTML report generated by Fuzzstorm, showcasing organized and visually appealing results with status codes and resource summaries.
See Fuzzstorm in Action
To give you a sense of how Fuzzstorm works, here’s a glimpse of the tool running in the terminal, scanning a target URL with a wordlist:
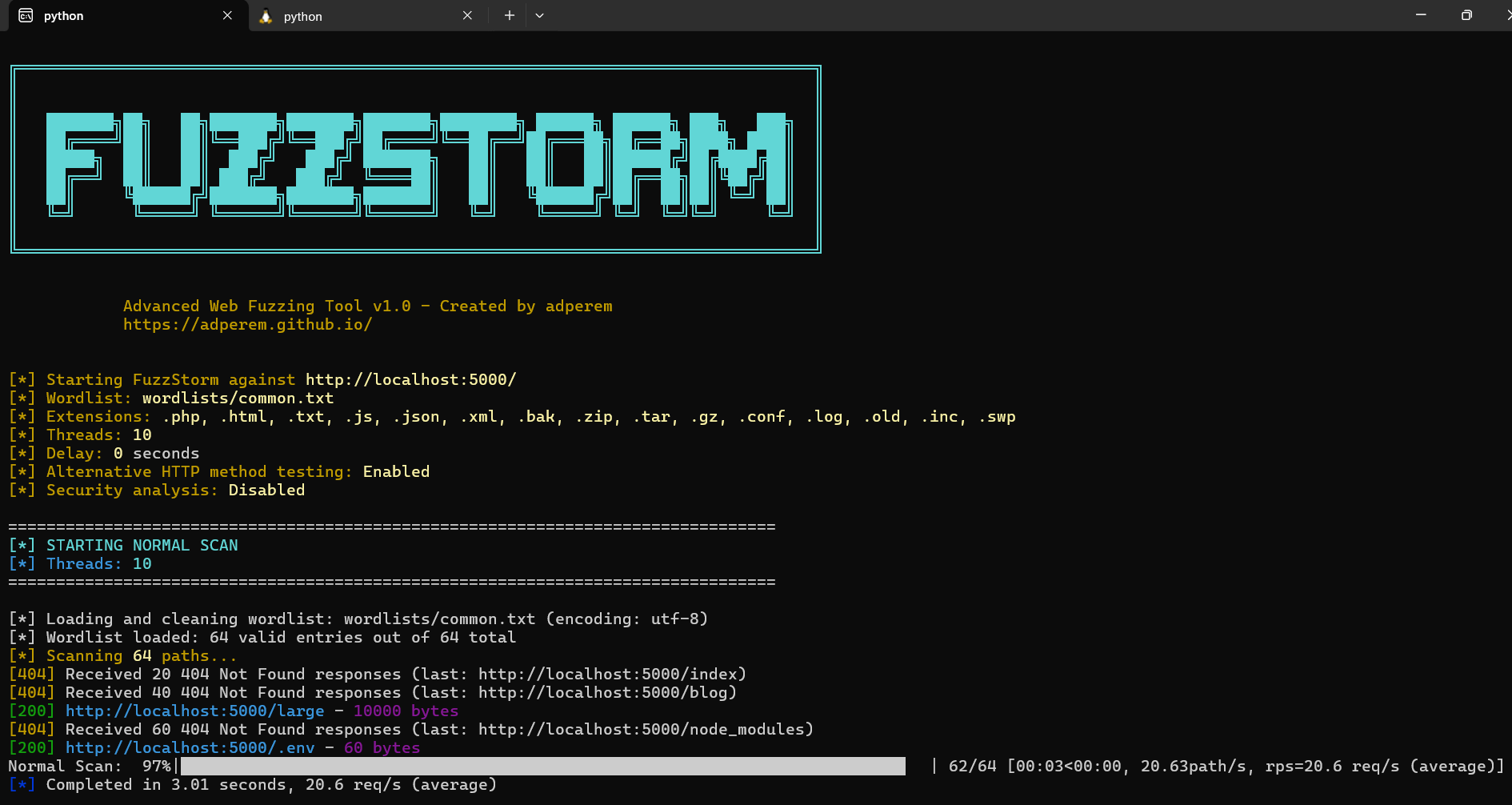
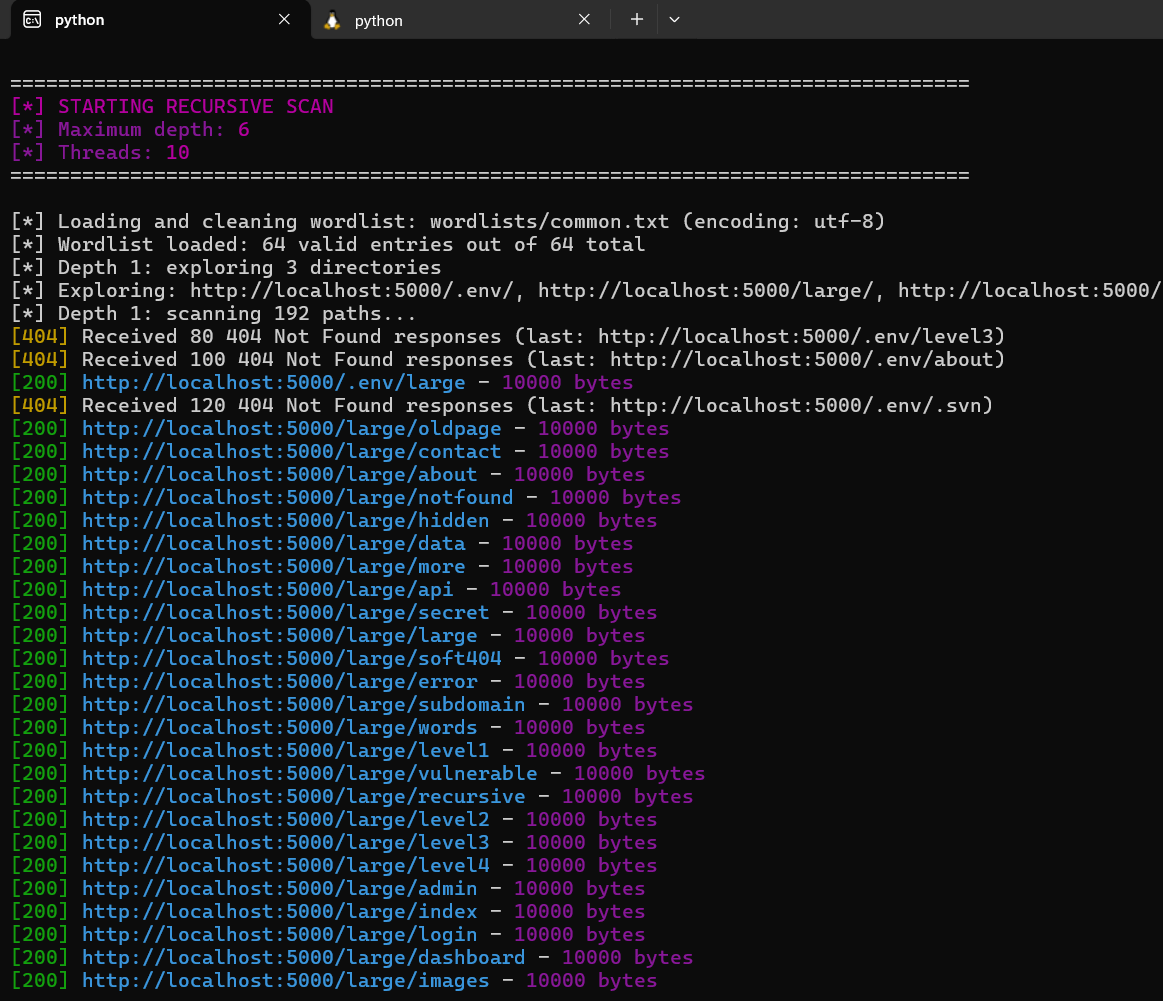
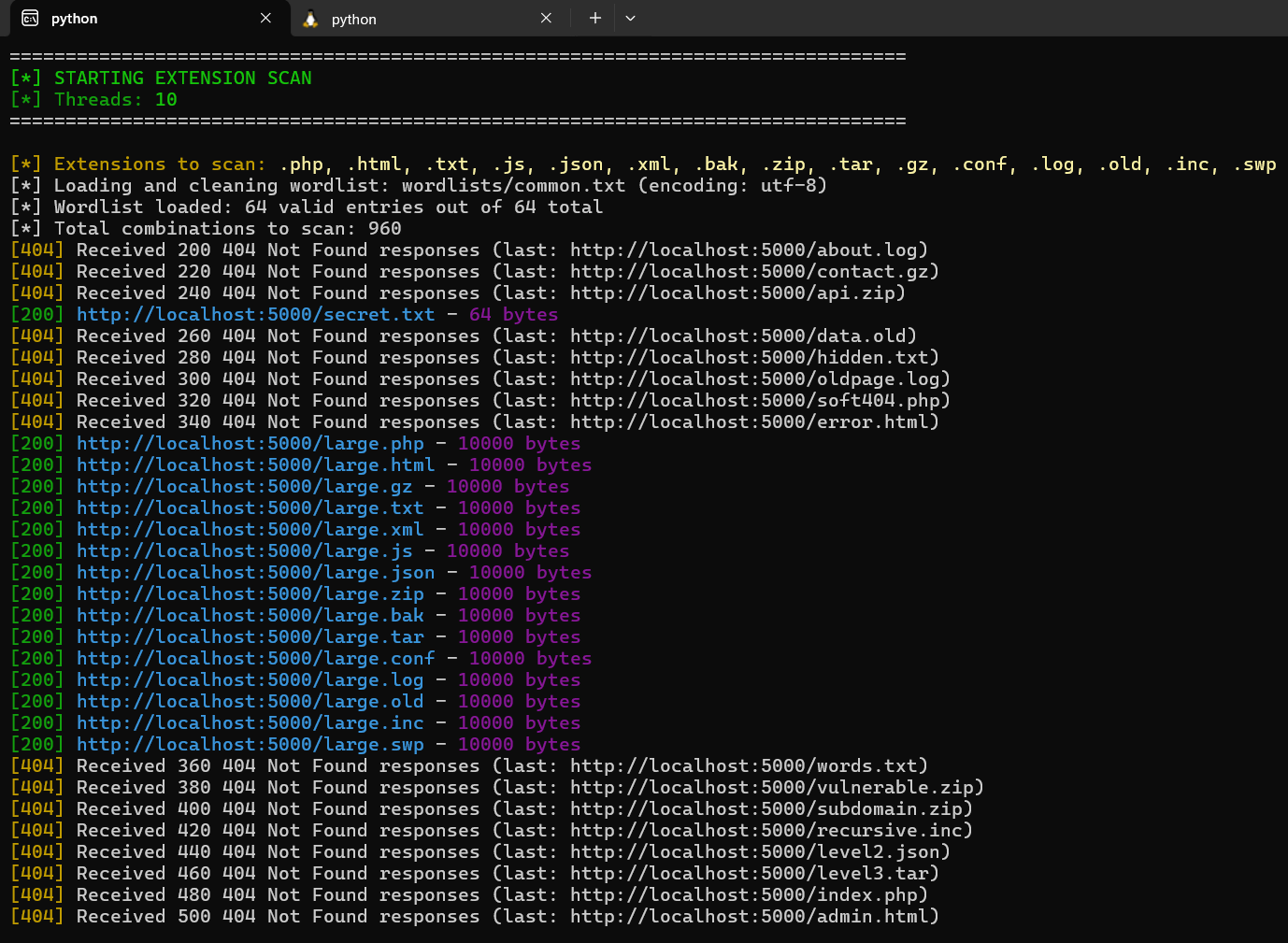 Fuzzstorm in action, performing a comprehensive scan with real-time output, including recursive and extension scans.
Fuzzstorm in action, performing a comprehensive scan with real-time output, including recursive and extension scans.
The execution is straightforward, and the results are automatically compiled into the stunning HTML report shown above, making it easy to analyze and share your findings.
How to Get Started with Fuzzstorm
Ready to revolutionize your fuzzing process? Fuzzstorm is open-source and available now on GitHub. Here’s how to dive in:
- Clone the Repository:
1 2
git clone https://github.com/adperem/fuzzstorm.git cd fuzzstorm - Install Dependencies:
1 2 3
python3 -m venv fuzzVenv source fuzzVenv/bin/activate pip install -r requirements.txt
- Run Fuzzstorm:
1
fuzzstorm -u http://target.com/FUZZ -w /path/to/wordlist.txt
Fuzzstorm will perform comprehensive scans, filter out soft 404s, and generate a beautiful HTML report with your results.
For detailed usage instructions, check out the Fuzzstorm README on GitHub. Join the Fuzzstorm Community Fuzzstorm is a community-driven project, and I’d love for you to be part of it! Whether you’re a developer, pentester, or security enthusiast, your feedback and contributions can help make Fuzzstorm even better.
⭐ Star the project on GitHub to show your support. 🐛 Report issues or suggest features via GitHub Issues. 💻 Contribute by submitting pull requests with enhancements or fixes.
Why Fuzzstorm is Essential for Web Security As web applications grow more complex, tools like Fuzzstorm are critical for staying ahead of attackers. With comprehensive scans, advanced soft 404 detection, and stunning HTML reports, Fuzzstorm empowers you to find vulnerabilities faster and present them with confidence. Whether you’re securing your own applications or hunting for bugs, Fuzzstorm is the tool you’ve been waiting for. Try Fuzzstorm today and experience fuzzing like never before! 🚀
Have questions or want to share your Fuzzstorm experience? Drop a comment below or reach out on GitHub. Let’s make web security stronger together!
